Access Control for Search
Protect your search infrastructure with fine‑grained access control. Create API keys with scoped permissions, restrict access by IPs and HTTP referers, define ACLs and rate limits, and collaborate safely across your team.
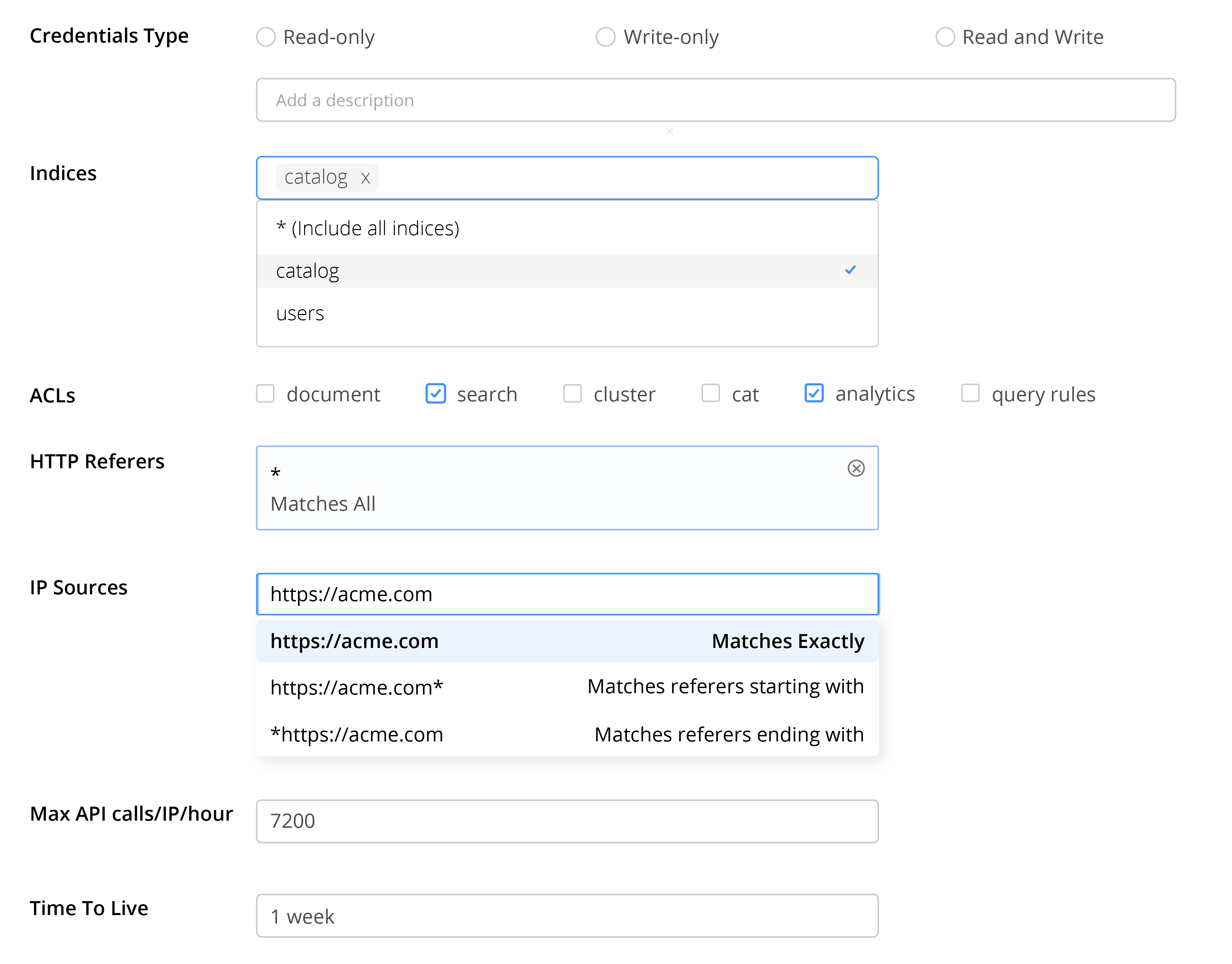
Powerful, Granular Controls
Everything you need to secure and tailor access to your search cluster.
Generate read, write or admin keys. Assign roles and tailor key-based permissions for different environments or applications.
Enforce network and origin restrictions to ensure only trusted sources can access your search cluster.
Apply fine-grained access controls, TTL and IP Rate Limit measures on your security keys.
Read, Write or Admin Keys
Issue environment or app specific API keys with clear, limited scopes. Rotate or revoke them anytime without downtime so you can keep usage isolated and secure.
 Role Based Access Control
Role Based Access Control
Assign roles for engineering, operations or analytics personas. Control who can create indices, modify pipelines, or view sensitive metrics—without sharing broad admin credentials.
 Restrict by IPs and HTTP
Restrict by IPs and HTTP
Lock down access to trusted networks or specific browser origins. Reduce attack surface and prevent unauthorized scraping or abuse.
Use ACLs
Apply ACLs to gate access to different operations. Combine with rate limits for consistent performance under load.
Filter Results by Fields
Expose only approved fields to downstream consumers. Enforce data minimization and keep internal attributes from leaking into public responses.
Collaborate With Your Team
Invite teammates, manage their access centrally and audit changes. Maintain velocity while ensuring security and governance standards are met.
Build secure search experiences
Start enforcing granular access policies in minutes.